What is information architecture and what is information infrastructure and how do they differ and relate to each other?
Describe how an organisation can implement a solid information architecture
It is essential for all organisations to implement a solid information architecture. Such architecture can be created by management during planning time and can be implemented on a daily basis by ensuring employees are aware of the objectives of different information systems such as hardware, software, services and their actual labour to ensure such processes are enforced to meet their objectives. Information architecture can also be implemented through the creation and adherence of a strong information security plan and also by managing employee access to databases. Data patches, which are pieces of software designed to solve problems or update programs using data as well as antivirus software such as Norton Anti-Virus can also be implemented to ensure solid information architecture is maintained within a firm. To ensure a solid information architecture exists within a firm, back up and disaster recovery systems should be enforced and data should remain secure.
List and describe the five requirement characteristics of infrastructure architecture
There are five key characteristics that a solid infrastructure architecture should consist of. Such characteristics include reliability, scalability, flexibility, availability and performance. It is essential for the infrastructure architecture of a firm to be reliable and dependable because this will ensure high accuracy and will prevent a firm from becoming in threatened. Scalability is another characteristic of infrastructure architecture and refers to the process of ensuring a firms systems meet growth requirements. Infrastructure architectures must also be flexible and be able to easily adapt to changing business demands and external competition. Availability is another key requirement of a solid infrastructure architecture and infers the necessity of a firms system to be available 99.999% of the time to ensure business continuity and success. Performance is an essential characteristic of infrastructure architecture and refers to how quickly a system can perform certain tasks for example processing a customers order. It is essential that the systems within a firms infrastructure architecture perform at an optimal speed to combat the growing pressure for systems to perform at a faster pace.
Five Characteristics of Infrastructure Architecture (Baltzan et al)
Describe the business value in deploying a service orientated architecture
A service orientated architecture is an architectural approach that integrates business services as linked, repeatable tasks. Such services communicate with each other through the transmitting of metadata and allow the re-use of applications/services creating an economical benefit. Service orientated architectures can add value to a firm is it allows businesses to ‘plug in new services’, upgrade existing services, respond swiftly and economically to changing market conditions. This allows the use of existing systems in different ways to meet different demands and is beneficial as it allows a firm to quickly and easily adapt to changing circumstances to meet varying demands. The other characteristics associated with service orientated architecture which add business value in deploying services include: (http://www.sun.com/products/soa/benefits.jsp)
- Improved business visibility: Integrated systems and aggregated data allow for a more consistent and accurate view of a firms customers
- Achieve Business Flexibility: Create an integrated, agile software infrastructure for quickly responding to business needs
- Gain Business Efficiency: Streamline, automate, and enable better tracking and visibility of your business processes
SOA
What is an event?
In terms of information technology, an event is an electronic message transmitted to ones computer that identifies something has happened. An event can also detect threats and opportunities and accordingly alert such messages to those who can make use and act on the information provided. According to ITIL Service Operation book, Page 35, an event is "any detectable or discernable occurrence that has significance for the management of the IT infrastructure or the delivery of IT service and evaluation of the impact a deviation might cause to the services”. E.g. new employee on a system
What is a service?
In terms of information technology, a service refers to the collaboration of a set of related commands that can be reused, such as a software products like Microsoft Word. Reusable services prove to be resource efficient as they reduce costs and improve productivity.
What emerging technologies can companies use to increase performance and utilize their infrastructure more effectively?
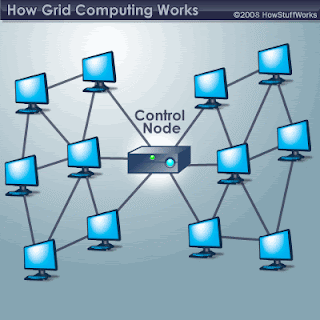
Grid computing is an emerging technology that can be employed by firms to increase their performance and to utilize their infrastructure more effectively. According to (http://www.wisegeek.com/what-is-grid-computing.htm), Grid computing is the act of sharing tasks over multiple computers. Tasks can range from data storage to complex calculations and can be spread over large geographical distances. Grid computing is beneficial to the performance and utilisation of infrastructure as it allows idle computers across the firm’s network to be employed for better use and also allows users to offer their free-processing time on home computers to firms. Other benefits that grid computing would create for businesses include:
- improved productivity and collaboration of virtual organisations
- widely dispersed departments to create virtual organisations
- creation of robust and flexible operational architectures
- allowing constant access to computing and data resources
(Business Driven Information Systems, Baltzan et al, 2010)
Graphical explanation of grid computing: (